A technology that has had a significant impact on organizations, large and small, is cloud computing. Numerous case studies have thrown light on how the cloud has revolutionized airlines, healthcare, banking, education, etc. Fundamentally, the cloud is the availability of resources (infrastructure, platform, software) that are provisioned via the internet. For the startup and enterprise, this means that there is no need to invest in expensive resources that are repeatedly becoming obsolete. By purchasing a cloud subscription, business owners can “rent” cloud resources thereby paying a fraction of the cost and there is no need to worry about configuration. The cloud allows users to provision resources (when the need arises) through a dashboard that also allows them to de-provision resources in lean times. For many organizations, the biggest problem is reducing operational expenditure because there is a constant need of funds for capital expenditure. The cloud does not advocate the reduction of any expenditure as the computation model supports IT operational expenditures as per demand. There are many cloud costing models like pay per use, billing on consumption, monthly subscription, etc.
Organizations are embracing the cloud due to many additional benefits it offers, for instance, geographic co-locations, support for multi-tenancy, and backup. Owing to these benefits and many more, the cloud is one of the most widely deployed risk mitigation strategies. What makes the cloud an even better option is the provision of software via the internet. Thus, popular and specialized software can be provided to the organization with by default support for updates, patches, and entitlement to new versions. This means the CTO does not need to worry about constantly having to buy new versions of software just because the previous is rapidly becoming obsolete. Moreover, software via the cloud is a very scalable provision since it authorizes software access as per need.
As organizations rapidly transition to the cloud, they are faced with a fundamental design issue. Initially, the cloud is adopted as a secondary resource that aids business function. With time, organizations embrace the cloud to an extent that the cloud becomes a lifeline technology without which the existence of organizations is under threat. Large amounts of data are placed by the many employees because the cloud can provide almost unlimited storage that is backed by a Service Level Agreement (SLA). The private cloud provisions data confidentiality by design which means that data is encrypted (encoding data into an alternate format that reveals nothing of the actual data) before storage on the cloud. It is worth noting that encryption/ decryption is a mathematically intensive algorithm that is designed to deter adversaries even if they had access to the algorithm. If such large amounts of data are stored on the cloud then searching the cloud for a keyword or a phrase would mean decrypting the entire cloud and carrying out the search. This operation is not easily executed due to the complex algorithms involved and the sheer scale of the data. The extreme overhead of decrypting large quantities of data and the risk of accidental exposure puts the user’s data at risk. What is needed is a way to search the large encrypted cloud storage without having to decrypt everything in storage. The other need is to carry out this operation with minimum computation and time cost.
The problem can now be addressed by Searchable Encryption. Searchable Encryption is an emerging cryptographic technique that allows search over the encrypted data stored on the cloud. Once a user outsources sensitive unencrypted data on the cloud, he loses control over the data and it may be misused without his prior permission. This prevents organizations and individuals from storing their data on the cloud and fully benefiting from the resources the cloud has to offer. Encrypting and outsourcing the sensitive data on the cloud gives you full control over your data and searching capability enhances the usability of the encrypted data across different business processes where data confidentiality is of utmost importance.
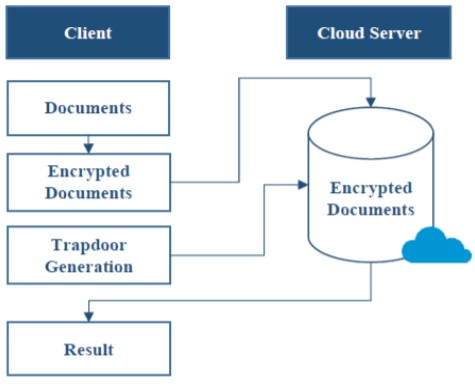
NUST faculty members, Dr. Hasan Tahir and Dr. Shahzaib Tahir, are looking into novel searchable encryption techniques that can allow search across a wide range of data types. Their research has been sponsored by a research grant from the National Center for Cyber Security (NCCS), Pakistan, and is proudly supported by their institutes. This research is based on utilizing homomorphic encryption which is a cryptographic mechanism that allows one to perform calculations on encrypted data without needing to decrypt it first. The result of the computation is in encrypted form and when decrypted, the output is the same as if the operations had been performed on the unencrypted data. Through this project, the faculty members will utilize homomorphic encryption to carry out computations directly over the encrypted data and identify the required data segments. Figure 1 represents the Searchable Encryption workflow. The proposed searchable encryption scheme will enhance the security and privacy related to the cloud, will reduce the network latency, and present a highly scalable solution. The proposed technology will have a profound impact across different verticals including healthcare, financial, e-commerce, document management etc.
The authors Dr. Hasan Tahir and Dr. Shahzaib Tahir are the Principal Investigator and Co-Principal Investigator respectively of the NCCS sponsored project titled “Privacy-Preserving Search over Sensitive Data Stored in the Cloud”, funded by the National Center for Cyber Security (NCCS). Dr. Hasan Tahir is the HoD, Department of Information Security, NUST School of Electrical Engineering and Computer Science, and Dr. Shahzaib Tahir is an Assistant Professor at the Department of Information Security, NUST Military College of Signals. They can be reached at hasan.tahir@seecs.edu.pk and shahzaib.tahir@mcs.edu.pk






