 For millenniums, mankind has been wearing clothes. For centuries, mankind has also been putting on devices like spectacles or ornaments like jewelry. In the era of technology, this evolution continues and has taken the shape of wearable devices like smartwatches, smart jewelry, smart clothing, etc. Medical scientists have also adopted these innovations and developed gadgets of their own like heart rate monitors, sleeping monitors, AI based hearing aids, fitness trackers, and so on. Take one-step ahead and you will see an evolution of wireless network of wearable computing devices. These types of networks, dubbed Wireless Body Area Networks (WBANs), are the talk of today’s network engineers and scientists aiming to develop next generation technologies as it offers many promising new applications in remote health monitoring, home/health care, medicine, multimedia, sports and many other potential applications.
For millenniums, mankind has been wearing clothes. For centuries, mankind has also been putting on devices like spectacles or ornaments like jewelry. In the era of technology, this evolution continues and has taken the shape of wearable devices like smartwatches, smart jewelry, smart clothing, etc. Medical scientists have also adopted these innovations and developed gadgets of their own like heart rate monitors, sleeping monitors, AI based hearing aids, fitness trackers, and so on. Take one-step ahead and you will see an evolution of wireless network of wearable computing devices. These types of networks, dubbed Wireless Body Area Networks (WBANs), are the talk of today’s network engineers and scientists aiming to develop next generation technologies as it offers many promising new applications in remote health monitoring, home/health care, medicine, multimedia, sports and many other potential applications.
A Wireless Body Area Network (WBAN) is defined as a network of miniaturized independent computing devices (e.g. sensors and actuators) that are situated in the clothes, on the body or under the skin of a person. The network typically expands over the whole human body and the nodes are connected through a wireless communication channel. Using short-range communication technologies, these devices talk to a designated centralized node (Hub) which further communicates with external networks via a Gateway. The general layout of a typical WBAN is illustrated in Figure 1.
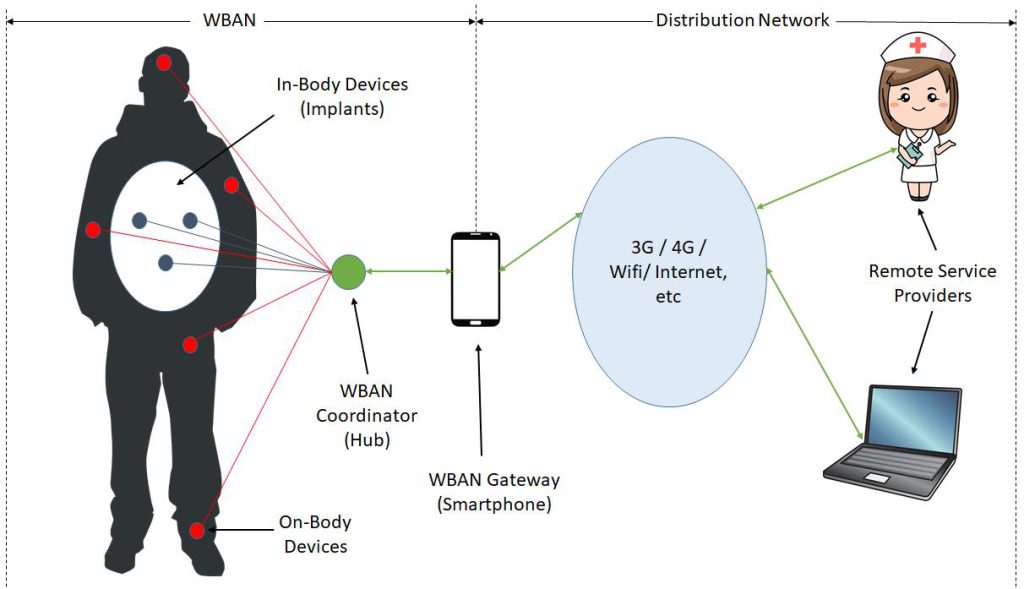
With every new technology comes the associated challenges and avenues for future evolution. Vulnerabilities that let hackers into the network are part and parcel of any type of modern network and hackers have been targeting these loopholes just like any other typical network, be it wired or wireless. Therefore, a special set of communication standard was developed by Institute of Electrical and Electronic Engineers (IEEE) keeping in mind the peculiarities of communicating in and around the human body. That standard, called IEEE Std 802.15.6, was published in 2012 specifically targeting WBAN. As high-power transmissions are harmful to humans and nodes in a WBAN are energy constrained, this standard provisioned an optional two-hop communication architecture to enable resource-constrained nodes to minimize transmissions when communicating with the Hub.
Although the developed standard addressed many challenges associated with the communication in WBANs, it still had some security weaknesses. The elliptic-curve based session key agreement methods of IEEE Std 802.15.6 were shown to have security weaknesses; it also did not provide the privacy features that should be expected of a WBAN. These security weaknesses were thoroughly studied by NUST faculty member Dr. Haibat Khan of NUST College of Aeronautical Engineering (CAE) and amendments were proposed to IEEE so that those security loopholes could be plugged in. In his work, titled “Pragmatic Authenticated Key Agreement for IEEE Std 802.15.6” two key agreement protocols which render a comprehensive range of security and privacy properties, which are regarded as essential for WBANs, are proposed. More specifically, the following has been proposed to IEEE for WBAN standard IEEE Std 802.15.6:
- Two new key-agreement protocols, named Privacy Preserving Key Agreement Protocol (PPKA-1 and PPKA-2), are proposed that overcome the security and privacy flaws in the existing key agreement protocols.
- A new formal security and privacy model has been developed in an appropriate complexity-theoretic framework and the proposed protocols have been proved to guarantee the requisite security and privacy properties within this model.
The proposed protocols were formally verified to withhold adversary attacks on victim. Subsequently, the proposed changes were forwarded to IEEE for official incorporation in the existing WBAN communication standard. The incorporation is awaiting further deliberation and final approval at IEEE working group level.
The author is a faculty member at College of Aeronautical Engineering (CAE), NUST, Risalpur. He received his PhD degree in Information Security from Royal Holloway, University of London. The research work was carried out in conjunction with ETH Zurich, Switzerland and Royal Holloway, University of London. He can be reached at hkhan@cae.nust.edu.pk.
Researcher’s Profile: https://bit.ly/37KZXoj




