Quantum key distribution (QKD) is a secure communication method that implements a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which then can be used to encrypt and decrypt messages. QKD is a secure communication method for exchanging encryption keys only known between shared parties. It uses properties found in quantum physics to exchange cryptographic keys in such a way that is provable and guarantees security. The security of traditional encryption methods relies on the computational complexity of mathematical algorithms. In contrast, QKD takes advantage of the fundamental principles of quantum mechanics, such as the uncertainty principle and the no-cloning theorem, to ensure the security of key exchange. While QKD provides secure key exchange, it does not directly encrypt the actual data transmission. After the key exchange, traditional encryption methods, such as symmetric encryption algorithms, are typically used to encrypt the data using the shared secret key obtained through QKD. QKD provides a foundation of secure key distribution that can be combined with existing cryptographic techniques to achieve end-to-end secure communication.
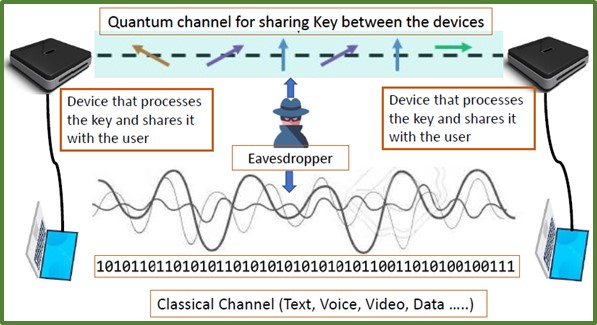
Figure below shows the general working principle of a QKD based encryption system. Two devices (shown as computers here) communicate with each other over the classical channel. The data sent between these devices is encoded and requires a key to decode it. This key is transmitted over the quantum channel. The main feature of the quantum channel which makes it suitable for the transmission of key is that the key gets destroyed if an eavesdropper tries to read it. Although the eavesdropper may be able to read some percentage of the key, he/she will not be able to generate an exact copy of that. Therefore, the user will know that someone has tampered with the secret key and they will discard that information.
Preparation: The sender (Alice) and the receiver (Bob) agree on a quantum channel, typically using a fiber optic cable, to send quantum bits (qubits) between them. They also established a classical communication channel for information about the quantum states.
Qubit Encoding: Alice encodes the information she wants to send to Bob into qubits. These qubits can represent the bits of a secret key.
Quantum Transmission: Alice sends the qubits to Bob through the quantum channel. Quantum states, such as polarization or superposition, are used to represent the bits.
Basis Choice: After receiving the qubits, Bob randomly chooses a basis (e.g., polarization direction) to measure each qubit. This choice is kept secret from Alice.
Measurement: Bob measures each qubit in the chosen basis and records the results. Quantum mechanics ensures that this measurement process is random, which is a crucial aspect of QKD.
Quantum Bit Comparison: Alice and Bob communicate over the classical channel, comparing the bases they used to encode and measure the qubits. If they used the same basis for a qubit, they keep the result as part of their shared key. If different bases were used, that qubit is discarded.
Error Rate Estimation: Alice and Bob use a portion of their shared key to estimate the error rate in their transmission. A high error rate might indicate eavesdropping.
Privacy Amplification: If the error rate is low and they are confident that no eavesdropping has occurred, Alice and Bob perform privacy amplification to distill a shorter, but more secure, shared key. This process involves applying a cryptographic hash function.
Secret Key Generation: The final shared key is generated and can be used for secure communication between Alice and Bob. It’s essential to ensure that this key is kept secret and is used for subsequent encryption, decryption, or authentication processes.
Security Analysis: Constant vigilance is required to monitor for potential eavesdropping attempts. If the error rate is too high or unexpected behavior is detected, the key generation process might need to be repeated.
The implementation of quantum key distribution (QKD) faces several challenges that need to be addressed for its widespread adoption and practical use. Some of the main challenges in the implementation of QKD are as follows:
Distance and Loss: QKD systems are sensitive to losses and noise in the communication channel. The distance over which QKD can be reliably implemented is limited due to the loss of photons during transmission. In practice, the achievable distance is typically limited to a few hundred kilometers using current technologies. Extending the distance and mitigating the effects of losses require advancements in techniques such as quantum repeaters or alternative methods like satellite-based QKD.
Practical and Robust Hardware: QKD systems rely on sensitive hardware components, such as single-photon detectors, photon sources, and quantum memories. These components need to operate reliably in real-world conditions and at room temperature to enable practical deployments. Developing cost-effective, robust, and efficient hardware is an ongoing challenge in the implementation of QKD.
Key Rate and Throughput: The key generation rate in QKD systems is typically lower compared to classical encryption methods. Generating secure keys at high rates to support real-time applications and high-throughput data communication is a challenge. Increasing the key generation rate without compromising security is an active area of research and development.
Practical Integration: Integrating QKD into existing communication infrastructures, protocols, and systems poses challenges. QKD needs to be seamlessly integrated with classical cryptographic algorithms and networking technologies to ensure end-to-end security.
Cost and Scalability: Currently, QKD systems are expensive to implement, making them less accessible for widespread deployment. Achieving cost-effective and scalable QKD solutions is crucial for its adoption in various applications.
Dr. Salman Abdul Ghafoor is working on this area with his research team. They have the following aims for this project:
- Identify the correct components and develop a laboratory.
- Implementation of the QKD protocol in a Laboratory environment.
- Integration of the QKD protocol based Encryptor with a classical communication link to demonstrate the encryption capability in a Laboratory environment.
- Implementation of the QKD protocol over larger distances of around 2 km for proof of concept.
- Integration of the long distance QKD code with a classical communication link.
- Commercialization of the Quantum encryptor by actively approaching clients such as banks and military institutions.
The author is Tenured Professor at the School of Electrical Engineering and Computer Science (SEECS), National University of Sciences and Technology (NUST). He can be reached at [email protected].
Research Profile: https://shorturl.at/irTU4

![]()





